Researchers at University of Cambridge have suggested through a new research that Android factory reset isn’t full-proof and there are lacunae which could prove dangerous for people who think that their device is not void of any personal data once it has been reset.
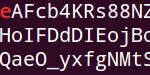
In a paper entitled “Security Analysis of Android Factory Resets“, Laurent Simon and Ross Anderson of University of Cambridge studied the implementation of Factory Reset on 21 Android smartphones from 5 vendors running Android versions v2.3.x to v4.3. Researchers found they were able to recover Google credentials on all devices. Though full-disk encryption could be a potential mitigation, they were even able to recover the encryption key from the devices which were factory reset.
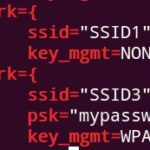
Researchers were able to recover “Conversations” (SMSes, emails, and/or chats from messaging apps) in all devices. They were also able to recover Gmail app emails, which were being stored in compressed form. They were also able to retrieve Whatsapp contacts with name and phone number and WiFi passwords.
Researchers note that for the sake of improved usability and user engagement, most smartphone apps replace passwords with authentication tokens the first time a user enters his / her password. After the first password based authentication, users are automatically logged-in with the authentication token; emails can be retrieved, calendar notifications downloaded, etc. without user intervention and these tokens are often stored on non-volatile flash storage on the data partition. There is a ‘master token’ that gives access to most Google user data.
To check if this can be retrieved and used, research factory reset their phone and then recovered the master token. They then created the relevant files and rebooted the phone. After the reboot, the phone successfully re-synchronised contacts, emails, and so on.
Researchers added that they were able to recover Google tokens in all devices with flawed factory reset, and the master token 80% of the time. Tokens for other apps such as Facebook can be recovered similarly, researchers added.
Researchers recommend that vendors use a recent eMMC with support for digital sanitisation, and to properly
expose it in the Bootloader, Recovery and Android kernels. Further, on reset erase the entire partition, not only the part explicitly used by the file system. This reduces the chance of unfortunate surprises due to eMMC wear-levelling block management and deletion implementation problems.
Researchers also recommend vendors should expose an option to have the Recovery mode perform a sanitisation validation, by reading back the entire partition and checking it.
Further, before a Factory Reset takes place, a broadcast Intent could be sent to apps, so that they could take necessary steps to invalidate their credentials – assuming that Internet connection is available.
The researchers also recommend storing the encryption metadata at the start of the data partition in a crypto header, rather than at the end in a crypto footer. This reduces the risk of dictionary attacks in the event of flawed sanitisation, since the first blocks are generally overwritten during partition formatting. Storing the metadata on the data partition also ensures that there is only one partition to take care of.