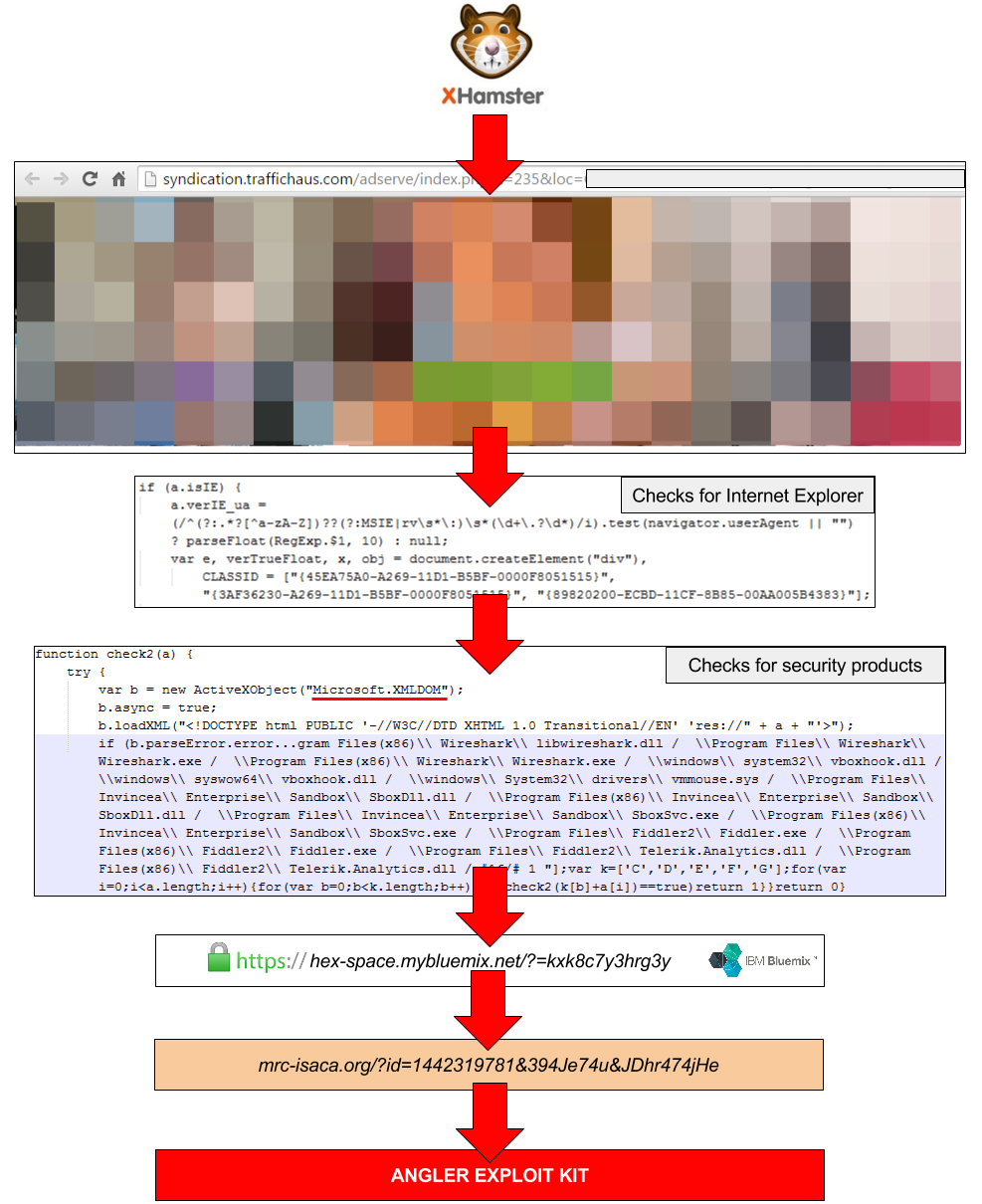
A number of top adult sites including xHamster have been targeted in a malvertising campaign that targeted Yahoo.com, MSN.com among others a few weeks back suggesting that the campaign hasn’t ended and has found new sites to attack more victims.
According to an analysis by Malwarebytes, malicious code is being delivered to victims’ computers over HTTPS connections through the use of top cloud platforms including Microsoft Azure, RedHat cloud platforms, and IBM’s Bluemix.
The malicious code is being delivered through an ad by TrafficHaus. The ad in question is about a certain sex messenger that eventually taking users to URLs which were serving the Angler exploit kit.
It was observed that there were multiple checks embedded within the ad to verify that the user is genuine and that they are running Internet Explorer. One of the vulnerability that was being used by the ad was the XMLDOM vulnerability (CVE-2013-7331) using which attackers were fingerprinting the victim’s system for particular security software, virtualization (Virtual Machines) and the Fiddler web debugger.
The benefit of such extensive checking is that attackers will only serve the exploit kit to real users and evade honeypots and automated requests, which may otherwise give away their real intent.
TrafficHaus did get a whiff of the attack and stopped this malicious campaign.
However, things didn’t stay the same and a new malvertising incident was reported which was a browser-based ransomware (browlock), also from xHamster. This browser-based campaign proves that malvertising may not infect your system with malware, but it could be as simple as locking up your browser.
Those sites are typically harmless but display alarming messages and annoying pop ups preventing users from closing their browser easily.