A security researcher has found a cross site scripting (XSS) flaw in Gmail for iOS app that gets triggered without any user intervention.
Roy Castillo, the researcher who found the flaw, notes in his blog that the XSS flaw was present in the “mail attachment” feature of the app. The researcher notes that the as the filename of the attachment wasn’t “escaped correctly”, the Stored XSS was triggered whenever the user opened an email with the specially named attachment.
“By using the generated report from Google Analytics I could inject script code that was executed on mail.google.com. The XSS is stored just simply reopen the mail anytime you want”, notes Castillo.
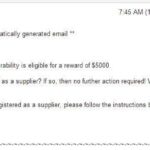
Castillo reported the issue to Google Security Team on October 8 and within two days the issue was fixed and he was rewarded $5,000 under bug bounty program.
“Google Security Team was pretty fast to address this issue and resolved this the next day itself. Google Security team awarded this bug with $5000”, notes Castillo.